Simplifying Manufacturing Companies Path to CMMC Compliance
Ensure your manufacturing operations meet Cybersecurity Maturity Model Certification (CMMC) requirements with ease and confidence using Trout's CMMC Compliance Software and Registered Practitioners. Simplify your compliance process and unlock Department of Defense (DoD) contracts.
- Home
- Solutions
- IT Compliance Solutions
- CMMC Manufacturing
Impact of CMMC Compliance on the Defense Industrial Base
Streamlining CMMC Certification Process
How Trout Software Simplifies the Journey to Achieving CMMC Compliance in the Manufacturing Sector
%20-%202024-09-11%20(1).png?width=120&height=120&name=The%20CyberAB%20-%20CyberAB%20Registered%20Practitioner%20(RP)%20-%202024-09-11%20(1).png)
Simple Hardware Integration
Add Trout hardware to your network, and let our CMMC Solution start building visibility and policies from your existing posture.
- Simple to install
- On-premise data processing tailored for CMMC requirements
- Extend your current systems and meet CMMC certification standards

.png?width=564&height=636&name=Group%20265%20(1).png)
Built-in protections
Implement CMMC enclave architecture with an intuitive UI to enhance visibility, security, and documentation.
- User-friendly UI for your IT team
- Deploy CMMC enclaves with Demilitarized LAN
- Enforce Access-Control, at the protocol level
- Built-in end-to-end authentication and encryption
- Get full log traceability
Best-in-class protections
Implement enclave architecture with an intuitive UI to enhance visibility, security, and documentation.
- Deploy Demilitarized LAN
- Enforce Access-Control, at the protocol level
- Built-in end-to-end authentication and encryption
- Get full log traceability
- All via a user-friendly UI
.png?width=564&height=636&name=Group%20265%20(1).png)
Something Powerful
Tell The Reader More
The headline and subheader tells us what you're offering, and the form header closes the deal. Over here you can explain why your offer is so great it's worth filling out a form for.
Remember:
- Bullets are great
- For spelling out benefits and
- Turning visitors into leads.
Automate CMMC Compliance Controls
Trout hardware natively addresses multiple CMMC certification requirements, and our team of CMMC Registered Practitioners is ready to support your IT team throughout the compliance process.
- Out-of-the-box coverage for key CMMC practices, including Access Control (AC), Identification and Authentication (IA), and System and Communications Protection (SC).
- Automated control collection and documentation to streamline your CMMC compliance efforts.
- Centralized Incident Response for enhanced security and quicker reaction times.

Demilitarized LAN (DLAN) Difference
Trout develop the Demilitarized LAN technology, which provides best-in-class protections and allows to streamline the CMMC certification process.








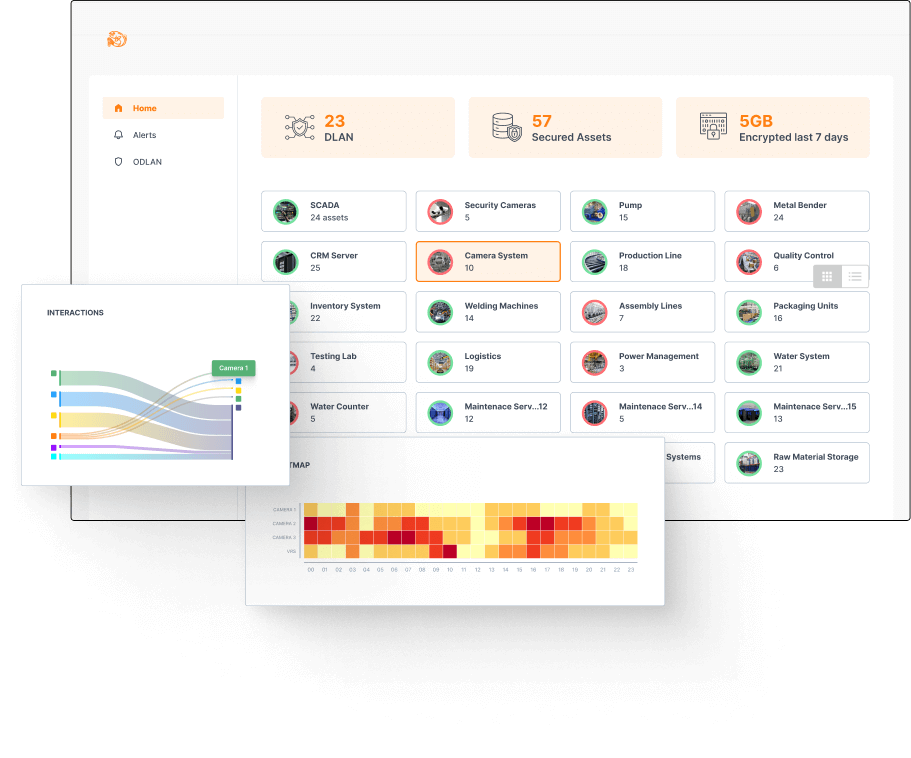
Plug and play CMMC solution to secure your industrial sites
At Trout, we work to help our customers deliver agile and secure networks, and to be able to tackle their digitalization efforts, from a strength position
Frequently Asked Questions
What is the relationship between CMMC and NIST SP 800-171?
Will CMMC 2.0 apply to all Department of Defense (DoD) contracts?
CMMC 2.0 will be required for DoD contracts once rulemaking is complete, which can take up to 24 months.
The specific CMMC level required should be clearly stated in the DoD contract or RFP; however, in alignment with Christian doctrine, the absence of such a specification should not be interpreted as a waiver of this requirement.