Sophos Firewall : 3 severe vulnerabilities found
Sophos Firewall : 3 severe vulnerabilities found
Explore Sophos Firewall vulnerabilities CVE-2024-12727, CVE-2024-12728, and CVE-2024-12729. Learn about risks like remote code execution and SQL injection, along with key mitigation strategies, including patching, MFA, and access restrictions, to stay secure.
📖 Estimated Reading Time: 3 minutes
Sophos Ltd. is a British security software and hardware company. It develops and markets managed security services and cybersecurity software and hardware, such as managed detection and response, incident response and endpoint security software.
Sophos showcased its investigative work through its well-known Pacific Rim operation. Over five years, this initiative delved into China-based groups that aimed at their firewalls. They discovered changing tactics involving botnets, new exploits, and custom malware. Additionally, they partnered with global cybersecurity organizations to pinpoint activities and bolster defense strategies.
Sophos Firewall is powered by SFOS (Sophos Firewall Operating System), designed specifically for the XGS Firewall hardware.
The XGS Firewall, following the XG and SG series, integrates both hardware and software to deliver network security via a web-based admin console.
It can be set up as a physical device at your location or in virtual and cloud spaces. This gives you flexibility for different setups.
Multiple Vulnerabilities have been discovered in Sophos Firewall, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could allow for unauthorized access on the system. Depending on the privileges associated with the system, an attacker could then; view, change, or delete data.
Vulnerabilities overview
This is the different Sophos vulnerabilities found recently in the Sophos Firewall :
CVE-2024-12727 A pre-auth SQL injection vulnerability
CVE-2024-12728 A credentials vulnerability potentially allows access via SSH
CVE-2024-12729 A post-auth code injection vulnerability allowing RCE
CVE-2024-12727 details A pre-auth SQL injection vulnerability in the email protection feature allowing access to the reporting database of Sophos Firewall could lead to remote code execution, if a specific configuration of Secure PDF eXchange (SPX) is enabled in combination with the firewall running in High Availability (HA) mode.
An external security researcher found the issue affecting roughly 0.05% of devices and responsibly reported it to Sophos through their bug bounty program.
The term "pre-auth" means that the attacker does not need to be authenticated to perform the attack. SQL injection, sometimes abbreviated to SQLi, is a type of vulnerability in which an attacker uses a piece of SQL (Structured Query Language) code to manipulate a database and gain access to potentially important information by placement via web page input for example, It is one of the most common web hacking techniques. A Remote Code Execution simply mean that the attacker can run malicious commands on the system remotely.
An attacker could gain access to the reporting database and by the same way acquire senstive information but the exploit becomes even more dangerous when a specific Secure PDF eXchange (SPX) configuration is enabled. SPX (Secure PDF eXchange) is a feature that encrypts email attachments before sending them, ensuring that only authorized recipients can view the attachments, if SPX is configured in a specific way in combination with the firewall running in High Availability (HA) mode, the attacker can escalate their access from just reading data to actually executing arbitrary remote code on the firewall.
Vulnerabilities details
CVE-2024-12727 details
The suggested and non-random SSH login passphrase for High Availability (HA) cluster initialization remained active after the HA establishment process completed, potentially exposing a privileged system account on the Sophos Firewall if SSH is enabled, affecting approximately 0.5% of devices. The issue was discovered by Sophos during internal security testing.
Attackers could attempt to access the Sophos Firewall system by trying to guess the default password with a tool like john-the-ripper, hydra or hashcat and then initiating an SSH connection. If the connection is establish the attacker would gain access.
CVE-2024-12729 details
A post-auth code injection vulnerability in the User Portal allows authenticated users to execute code remotely in Sophos Firewall older than version 21.0 MR1 (21.0.1).
"Post-authentication” means the attacker needs to have valid credentials ( obtained through phishing, credentials reuse or weak&guessable credentials) and must log into the system (in this case, the User Portal of the Sophos Firewall) before exploiting the vulnerability. Code injection occurs when an attacker can insert and execute their own code on a system.
After logging in, the attacker can exploit a specific vulnerability in the User Portal's code. This flaw improperly handles user input, allowing the attacker to insert malicious code or commands.
Mitre ATT&CK Mapping and Cyber Kill Chain
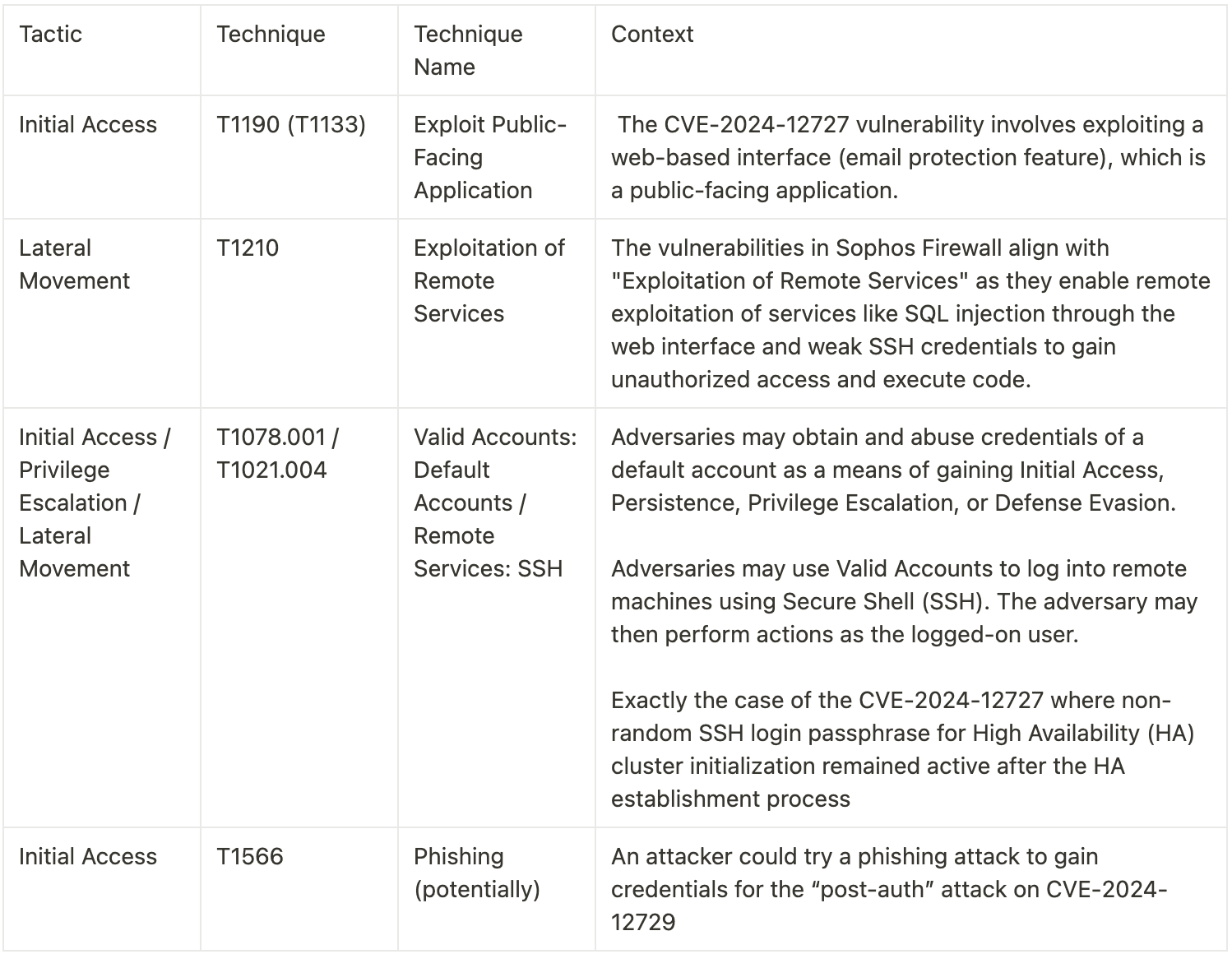
Mitigations
Limit access to the User Portal and Admin Console to trusted IP addresses or internal networks only.
Avoid exposing these interfaces to the public internet unless absolutely necessary.
Enforce Strong Password Policies
Brute-Force Attacks defenses like :
Limited login attempts
MFA for all users
Disable SPX (Secure PDF eXchange) and HA if Not Required
Use VLANs and other segmentation techniques to limit lateral movement in case of compromise.
User Behaviors monitoring to detect suspicious commands use
Specific Sophos recommendations:
Apply appropriate updates provided by Sophos to vulnerable systems immediately after appropriate testing.
CVE-2024-12728
To mitigate the issue of the SSH passphrase (used during deployment of HA ports) remaining active, customers can ensure that:
SSH access is restricted to only the dedicated HA link that is physically separate, and/or
HA is reconfigured using a sufficiently long and random custom passphrase
Sophos recommends to disable WAN access via SSH by following device access best practices and instead use VPN and/or Sophos Central for remote access and management.
CVE-2024-12729
Customers can protect themselves from external attackers by ensuring their User Portal and Webadmin are not exposed to WAN. Sophos recommends to disable WAN access to the User Portal and Webadmin by following device access best practices and instead use VPN and/or Sophos Central for remote access and management.
Summary
Recent findings about Sophos Firewall vulnerabilities highlight significant cybersecurity risks for organizations. The vulnerabilities—CVE-2024-12727, CVE-2024-12728, and CVE-2024-12729 — can lead to remote code execution and unauthorized access.
CVE-2024-12727 involves a pre-auth SQL injection vulnerability that may expose sensitive data, especially with certain configurations like Secure PDF eXchange (SPX). CVE-2024-12728 stresses the importance of strong SSH password practices to prevent unauthorized access. CVE-2024-12729 shows the risk of post-auth code injection that could be exploited by authenticated users.
Organizations using Sophos Firewall should take action to apply patches, restrict access to critical interfaces, enforce password policies, and implement additional security measures such as multi-factor authentication (MFA). Staying proactive in cybersecurity will help protect networks against threats.