INDUSTRIAL CYBERSECURITY & COMPLIANCE
Plug & Play Cybersecurity for physical environments
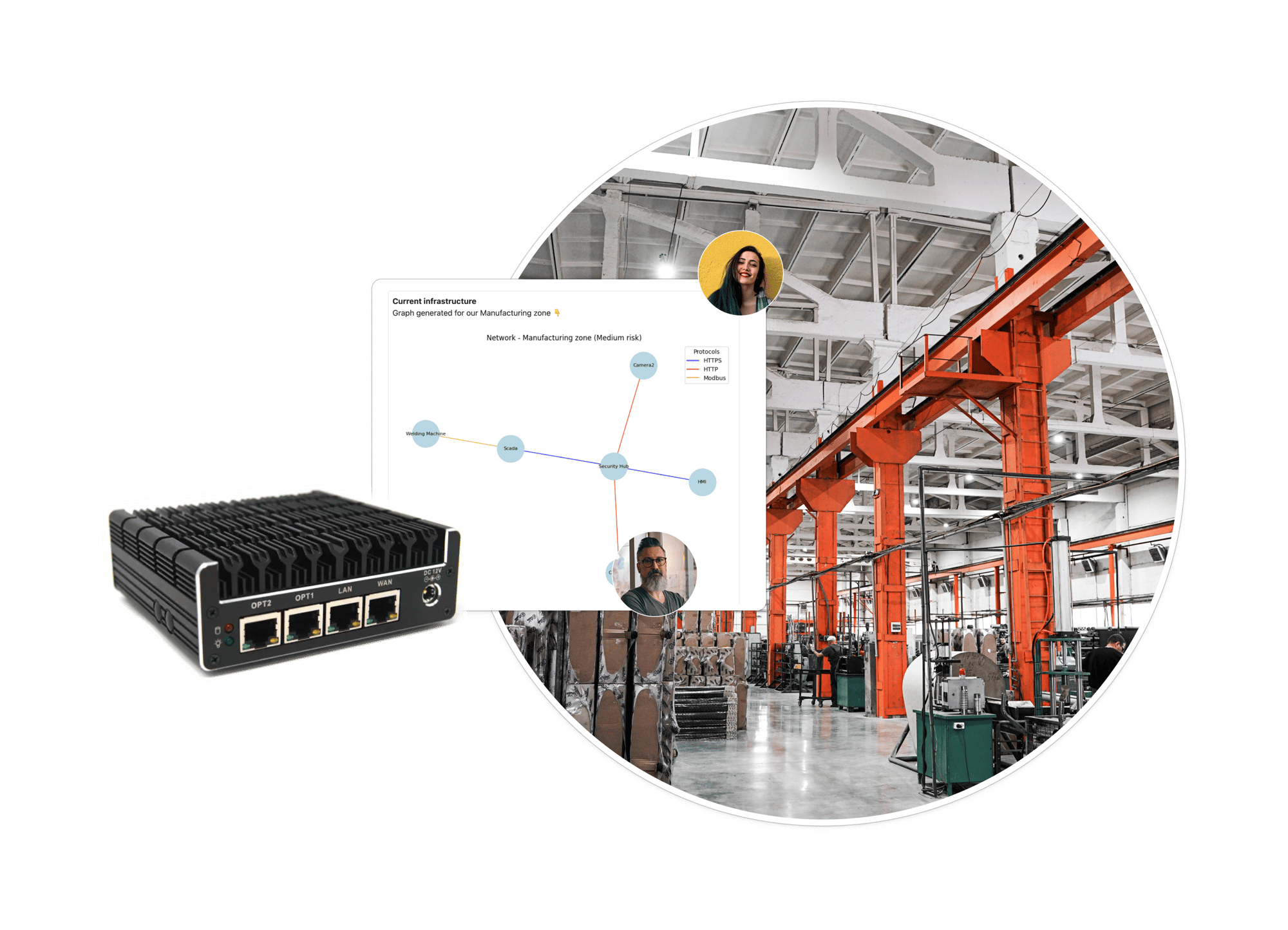
Trout Software's Cyberbox is a simple hardware, installed on your site's network. It provides a package solution to protect industrial environments from cybersecurity threats & automate information security compliance.
Real time threat monitoring in hours, not weeks, and automated compliance that saves hundreds of hours yearly
-
Assets
-
Networks
-
Detections
-
Events
-
Compliance
ASSETS DISCOVERY & MANAGEMENT
Build and maintain asset inventory in minutes
Install Trout Cyberbox on your site by simply connecting our hardware to your network. This will instantly build an asset inventory. Trout OT UI enables you to enrich your inventory with organizational context, such as equipment information, maintenance schedules, and ownership details.
Quickly establish your baseline, and Trout Cyberbox will run in the background to detect moving, new, or disappearing assets.
NETWORK SEGMENTATION
Define and secure network zones without rewiring your site
From your asset inventory, Trout OT UI allows you to define network segments and conduits, following NIST guidelines.
By layering Trout Core Engine, the Cyberbox is able to analyze traffic, enrich with organizational context, and enforce a security policy to your network, paving the way to deploy Zero-Trust in your physical sites.
KILL CHAIN DETECTIONS
Smart threat detections, correlating signals to filter out the noise
Trout OT Threat Intelligence team continuously builds detections and push them to live Cyberboxes.
Trout Core Engine then processes signals on-site, across networks, logs and configurations, matches them to known attack vectors to detect relevant threats.
LOG SKIMMING
Process, enrich and forward logs to your central security stack
Trout Cyberbox processes on-site signals, across networks, logs and configurations. By using Trout OT UI, your team can define which events are of interest and that you would like to ingest in your central security stack.
Gain visibility without overloading your systems with noise.
CONTINUOUS BACKGROUND COMPLIANCE
Deploy background controls across your physical sites to accelerate your compliance
Leverage Trout's Industrial Compliance Starter-pack - ISO, ANSSI, NIST, IEC - to implement processes and controls, within your sites, in line with strong standards. Through Trout OT UI, your team can customize controls and enrich these with your specific organizational context.
Each scheduled audit will collect proofs and tie them to specific controls, allowing to accelerate your compliance efforts.
Integrate your industrial footprint in your existing security tooling
Trout OT allows you to extend your current solutions (e.g. SIEM/SOC) to new environments. Our solutions allow the processing of logs via Trout Core Engine, and to skim the relevant information to these solutions.
Increase visibility, and compliance controls, while keeping the noise down.



.png?width=429&height=117&name=images%20(1).png)




.png?width=388&height=130&name=images%20(2).png)
STBMA secures ski resorts with Trout
Téléportés Bettex Mont d'Arbois (S.T.B.M.A), a premier ski resort operator nestled in the heart of the French Alps, has been synonymous with exceptional alpine experiences for decades. To elevate its operational efficiency and ensure the highest level of security for its network and Operational Technology (OT) systems, STBAM embarked on a digital transformation journey by integrating Trout Cyberbox into its network infrastructure.
%20(1).webp)
10 Steps to Protect Industrial Environments from Cyber Threats
A comprehensive 10-Step Strategy designed to strengthen the cybersecurity defenses and resilience of industrial companies.
Protect Your Industrial Environments Today
Trout Software’s Cyberbox is a simple hardware that is installed on your site’s network.
It provides a package solution to protect industrial environments from cybersecurity threats & automate information security compliance.